hey,
aliyev has started a new war in Artsakh, killing peaceful citizens, ruining cities, taking captive those who has not managed to run away. And I want to ask why?
I’m 28 years old and I have seen three wars already. And I want to ask why?
Antranig was trying to explain me that yes, sure, war sucks, he has seen more wars in his life and has lost more people than I have. And I want to ask why?
So I opened my laptop today and this is what I saw.
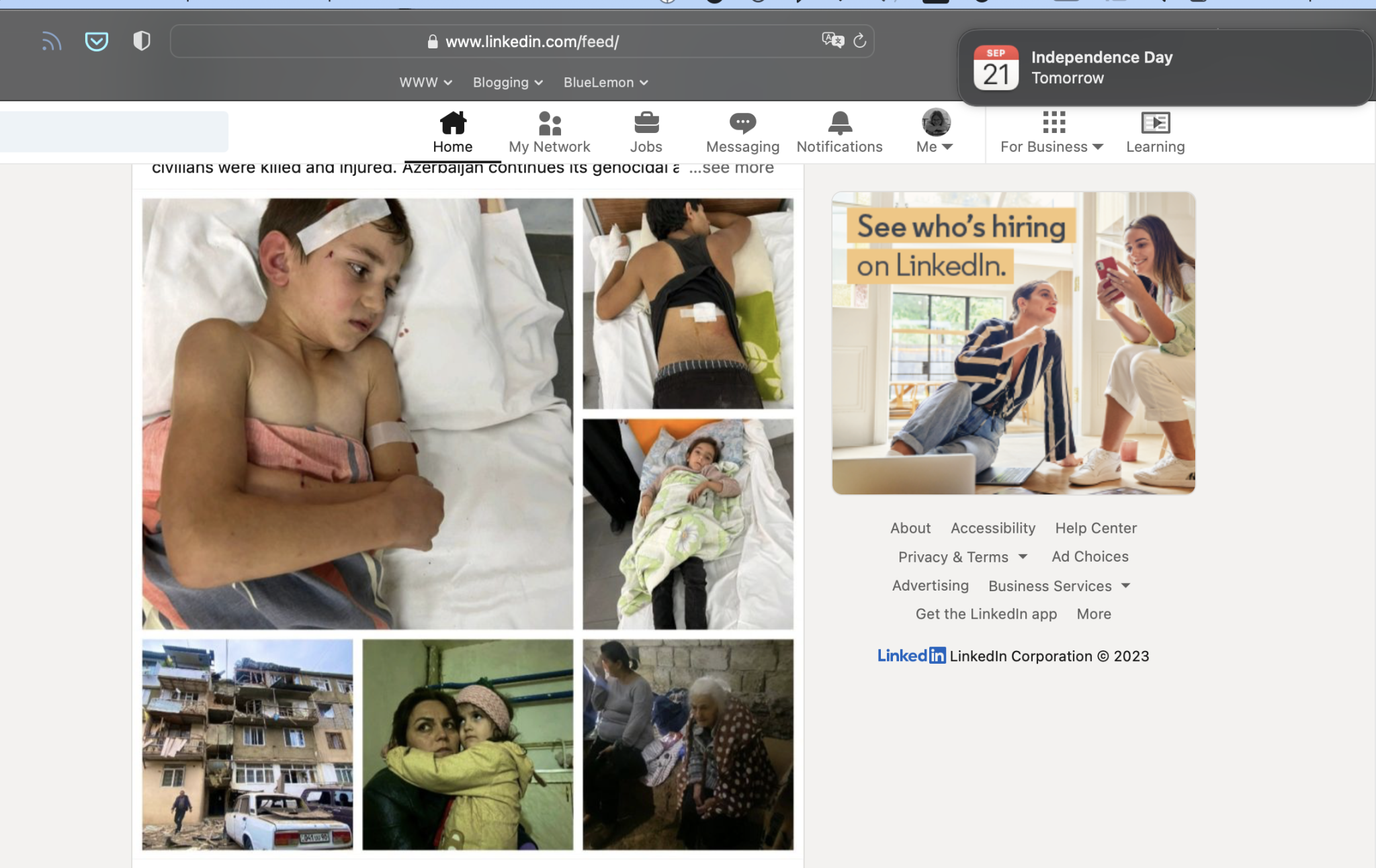
And I want to ask “why”?
And then I just scroll the feed, swallow news, swallow reality, swallow tears, and the only thing that I want to understand is “why?”.
There is nothing much to do right now, all my friends keep asking: what can we do, should we protest, should we fight, should we go and scream at their faces for not doing anything and I ask them “why?”.
After I told one of my friends that I am unable to work today because of the war he was like: “its hard to believe how many wars are there in the world, given the fact that most people don’t want war. I will never understand that…” Yep, me neither, so I am asking “why”?
I am talking to one of my colleagues living in India, I’m showing him what’s happening here, how we lost a whole country in less than 24 hours and he tells me about his country, how the same political sh*t is happening there and how he wants to leave the country to live in peace. And I am asking “why?”
I hear people screaming outside of my house, inviting everyone to join and protest. I don’t think they have a better alternative so I am just looking at them thinking “why?”.
The kids go to school, not even being properly dressed or fed because of the blockade. They want to study, they want to be a better citizens for the future of their country, they want to be the change they want to see. And they hear bombing in the middle of the lesson, can’t even go back to their parents. Why?
I am not saying Armenians are special, I’m not saying this is happening only with us. We are just one of those who are not protected. Who don’t have enough oil or gold or gas to close some eyes, and deafen some ears. We are not preferable. We do not deserve. Why?
The war sucks, the world sucks, my news feed sucks, all governments suck, and politics sucks.
And I am not leaving. I am staying. And do you know why? Just because that’s what you want for us. Staying in spite of you.
I thought it’s supposed to be easier…