Hey there,
These days I’m concentrating myself on improving my hacking skills, because I can’t afford this dream of mine to stay on my journals, some dreams have to come true. I read, I try to hack some servers (there is nothing illegal, mum), I blog about my solutions, I blog about the way I search the solutions, because I’m only a beginner in the field, not an expert – beginner.
I was too suspicious about my abilities. I always am. Sometimes I challenge myself in order to show the girl in the mirror that she can, sometimes I ask for an opinion from someone who knows me better than I know myself. I will never take up a task or a job out my ability scope. So, in order to avoid a situation like that I always update my knowledge about my skills.
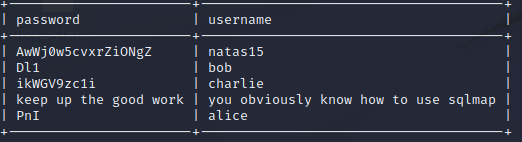
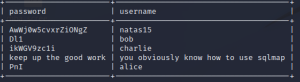
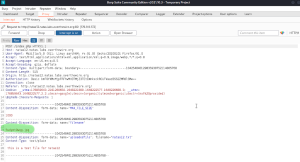
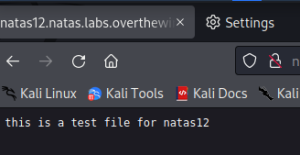
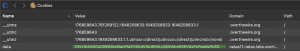
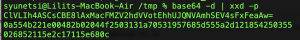
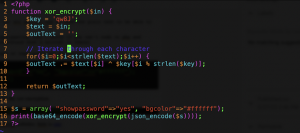
The 5th of November should be marked on my calendar. Today I found out that I’ve finally learnt to understand the problem. As a beginner hacker I would always worry about the solution not even understanding the core problem or the task itself. Today, as I was doing one of the levels of OverTheWire-Bandit, I had no idea which command should be used, the only thing I knew was that the file contains a human-readable string.
What would a beginner do in this case? Of course, I googled how to find a human readable string in a file. And there was the solution:
strings somebinaryfile | grep textuwanttofindMaybe you’ll think: “WTF, nothing serious, you haven’t discovered anything girl, you’ve just googled about it and copy-pasted the solution”. For me this is a relevant point on my learning path, because I finally googled the problem not the solution.
Before finding that link I read so many man pages of strings or grep and learnt some things I had no idea about. Anyway, I learnt the art of reading and understanding the problem. And didn’t worry about the solution.
So, if you are beginner, this can be a good tip for you: never worry about finding the password of this or that level. Maybe you will never be able to find the password, but the reading, the research that you do, the knowledge you gain, will help you to become the specialist you want to be. Try to understand the main problem of the task and don’t give up until you solve it.
thought it’s supposed to be easier…