hey there,
so you have already passed all the previous levels, congrats, you are good to go! it’s getting a bit complicated from now on. No worries! I’m here to make it easier for you. Now we are on level 11, and I hope you have the password.
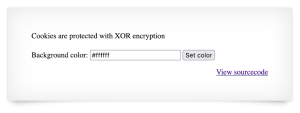
What do we see here?
you already know what to do, right? let’s see what the sourcecode says:
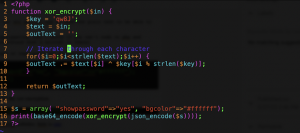
$defaultdata = array( "showpassword"=>"no", "bgcolor"=>"#ffffff");
function xor_encrypt($in) {
$key = '<censored>';
$text = $in;
$outText = '';
// Iterate through each character
for($i=0;$i<strlen($text);$i++) {
$outText .= $text[$i] ^ $key[$i % strlen($key)];
}
return $outText;
}
$defaultdata array contains two values: showpassword and bgcolor. (you do see that “no”, do you? we are gonna change that to “yes”)
what is on the next line? xor_encrypt? what a new hell is this? let me explain: XOR Encryption is like two salads with one same ingredient – the key. in both cases (Encryption and Decryption) the key stays the same. if the plain text has the same length as the key, it’s used once, if not – key is repeated. here I’ve found a very simple
explanation of the concept for you.
now that we know what xor encryption means, let’s go on and look at the rest of the sourcecode.
function loadData($def) {
global $_COOKIE;
$mydata = $def;
if(array_key_exists("data", $_COOKIE)) {
$tempdata = json_decode(xor_encrypt(base64_decode($_COOKIE["data"])), true);
if(is_array($tempdata) && array_key_exists("showpassword", $tempdata) && array_key_exists("bgcolor", $tempdata)) {
if (preg_match('/^#(?:[a-fd]{6})$/i', $tempdata['bgcolor'])) {
$mydata['showpassword'] = $tempdata['showpassword'];
$mydata['bgcolor'] = $tempdata['bgcolor'];
}
}
}
return $mydata;
what does it say? look at the 5th line.
$tempdata = json_decode(xor_encrypt(base64_decode($_COOKIE[“data”])), true);
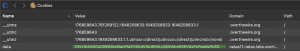
hah! Cookie? So we must pay attention to the cookies, there should be something for us.
"Cookies are protected with XOR encryption" says the page. not only that, if you've already paid some attention, $tempdata has played some games: json_decode, xor_encrtpt and then base64_decode. What we can do is to start from the end.
1) base64 decoding our favorite line of the cookies (base64 -d)
2) in order to be able to do some xor_encrtypt, we need a hexdump, so
3) base64 -d | xxd -p
note: you’ll see %3D at the end of the cookie, which is URL encoding, basically it is a =, so replace that part with =.
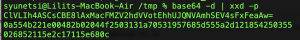
the result should look like this:
4) now we have the output of our xor_encrypt and we need the plain text to be able to find out the key.
here comes some php coding copy-pasting (don’t worry if you can’t code in php and remember, you just need to understand what’s written in there)
just create a php file and type or copy-paste the following.
<?php
$in = array( “showpassword”=>”no”, “bgcolor”=>”#ffffff”);
print(json_encode($in));
?>
the output is going to be our input for the XOR encryption.
{“showpassword”:”no”,”bgcolor”:”#ffffff”}
the world is full of encrypting – decrypting websites. here is
one:
voila! we have our key: qw8Jqw8Jqw8Jqw8Jqw8Jqw8Jqw8Jqw8Jqw8Jqw8Jq
if you remember, I have already told you, that in case the key is short, it is repeated. so the exact key is: qw8J
our crazy mind says: go and copy some other code out there.
go back to your php file and do some edits. I had told you we were gonna make the “no” into a very nice “yes”.
execute the file, and you will see a whole another cookie there:
ClVLIh4ASCsCBE8lAxMacFMOXTlTWxooFhRXJh4FGnBTVF4sFxFeLFMK
what is required is to replace the previous one with this new, much better one. and please, don’t forget to add %3D at the end. the rest is on you! enjoy the moment of seeing the password on your screen. you deserve it!
I thought it’s supposed to be easier…